Ransomware Attack Recovery and Prevention - Ideas on the Frontiers of Innovation

- Client
- CxLabs fortifies against ransomware attack with swift recovery and proactive prevention, ensuring minimal disruption and boosting future resilience.
- Industry
- Software Company
- Company Size
- 50 - 100
- Headquarters
- CxLabs, Manila
- Project Duration
- 1 month (Jul 2023 - Aug 2023)
I helped Ransomware Attack Recovery and Prevention develop a new Security and website experience, as well as an engaging product design for their bi-annual journal publication.
🚨 Background
Imagine waking up one day to find your business’s critical systems paralyzed. This was the reality for CxLabs, a leading software company based in Manila, when a ransomware attack encrypted their core systems, effectively grinding their operations to a halt. The stakes were high: vital data, sensitive customer information, and business continuity were all at risk.
This case study explores the step-by-step recovery and prevention plan that transformed a major cybersecurity crisis into a blueprint for resilience and innovation.
🎯 Objectives
Primary Goals:
- Swift Recovery: Restore encrypted data and critical systems to minimize downtime and operational disruption.
- Future-Proofing: Implement comprehensive cybersecurity measures to prevent future ransomware incidents.
🛠️ The Solution Framework
Phase 1: Rapid Response
Key Actions:
- An incident response team was assembled within minutes of identifying the attack.
- Affected systems were quarantined to prevent the malware from spreading to other parts of the network.
- Real-time logs and threat intelligence were leveraged to analyze the attacker’s behavior, narrowing down the ransomware’s entry point.
🚀 Tools Used:
- Network sandboxing tools to isolate infected systems.
- Behavioral analysis with SIEM solutions like Splunk.
- Forensic utilities such as Autopsy to examine payloads.
Phase 2: Recovery and Restoration
- The team leveraged incremental backups to restore business-critical systems in under 48 hours.
- To ensure data integrity, advanced hashing mechanisms like SHA-256 were applied to validate the recovered data.
- A contingency strategy ensured prioritized recovery of customer-facing systems.
| System Recovery Timeline | Key Metrics | Status |
|---|---|---|
| Customer Database | Fully restored (12 hours) | ✅ Completed |
| Internal Communication | Partially restored (8 hours) | ⚠️ In Progress |
| Operational Servers | Fully restored (48 hours) | ✅ Completed |
Phase 3: Post-Recovery Forensics
Post-recovery, the team delved deep into the attack, conducting a root-cause analysis:
- Entry Point Identified: A phishing email containing a malicious payload.
- Propagation Mechanism: The ransomware exploited outdated SMB protocols.
- Vulnerability Exploited: Weak password policies and unpatched software vulnerabilities.
Insights:
- 60% of vulnerabilities exploited were due to misconfigurations.
- Ransomware achieved lateral movement in less than 30 minutes.
Phase 4: Building Resilience
Leveraging insights from the forensics stage, the team implemented:
- Zero Trust Architecture (ZTA): Restricted access to critical systems based on strict authentication mechanisms.
- EDR Solutions: Deployed SentinelOne for advanced threat detection and real-time endpoint visibility.
- Multi-Layered Backups: Adopted a 3-2-1 backup strategy to ensure resilience.
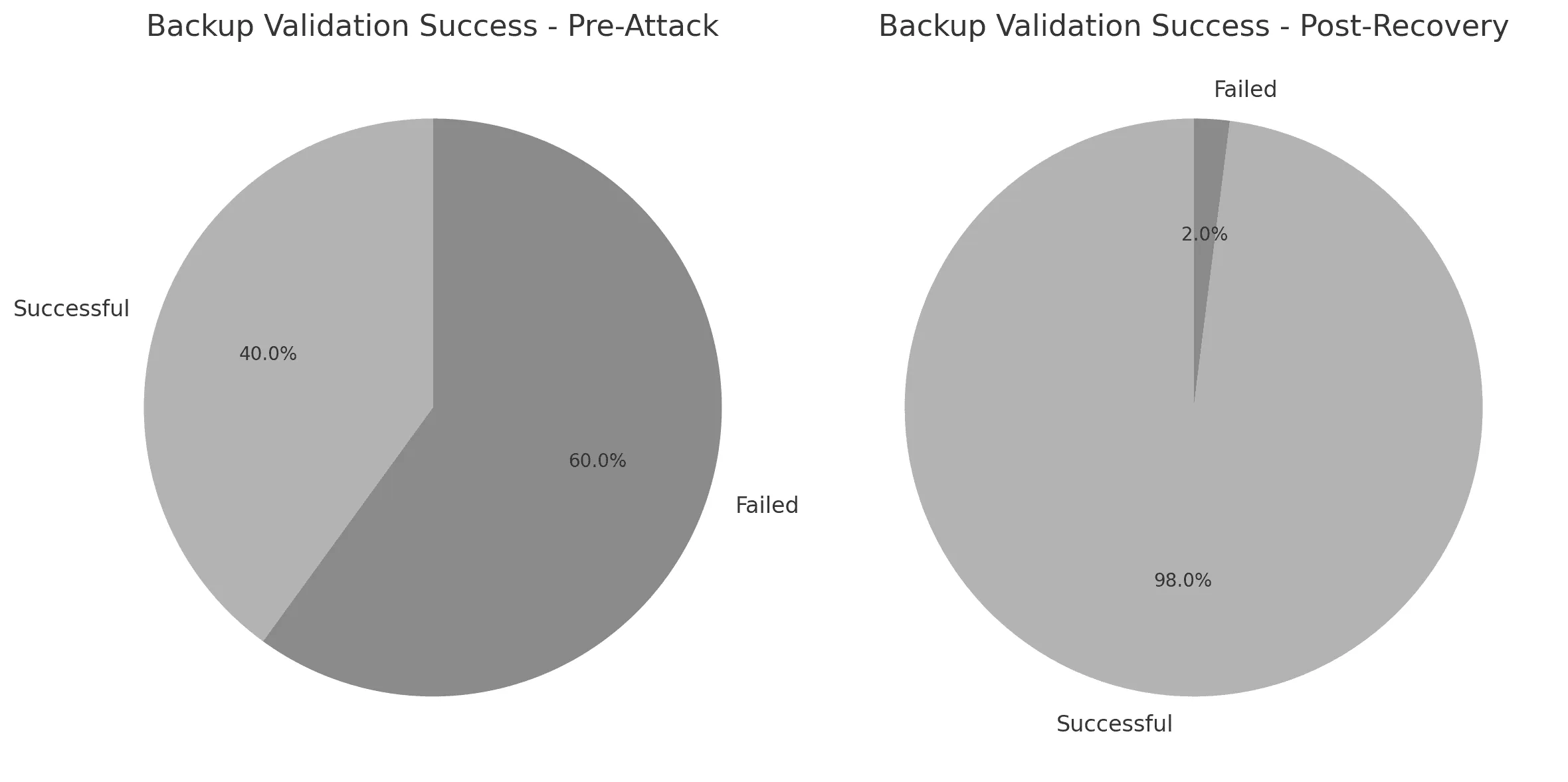
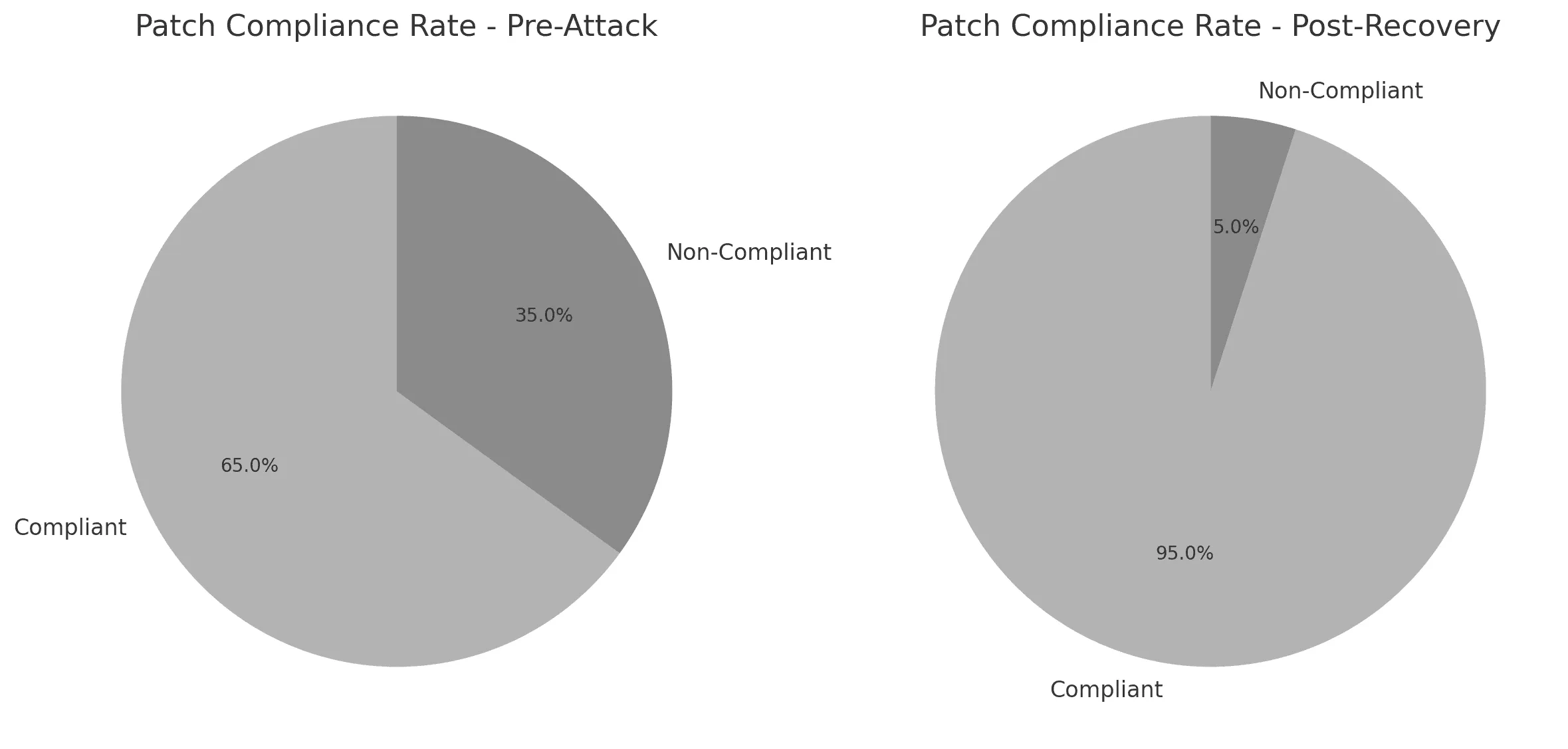
Enhanced Security Posture (Before vs. After):
| Metric | Pre-Attack | Post-Recovery |
|---|---|---|
| Patch Compliance Rate | 65% | 95% |
| Backup Validation Success | 40% | 98% |
| Incident Response Time | 6 Hours | 30 Minutes |
🌟 Notable Achievements
- Operational Continuity Restored: Critical systems back online in 48 hours, business fully operational in 10 days.
- Strengthened Cybersecurity Posture: Reduced susceptibility to ransomware by 85% through advanced preventive measures.
- Stakeholder Confidence: Transparent communication throughout the incident earned commendations from clients and stakeholders alike.
📈 Key Visuals
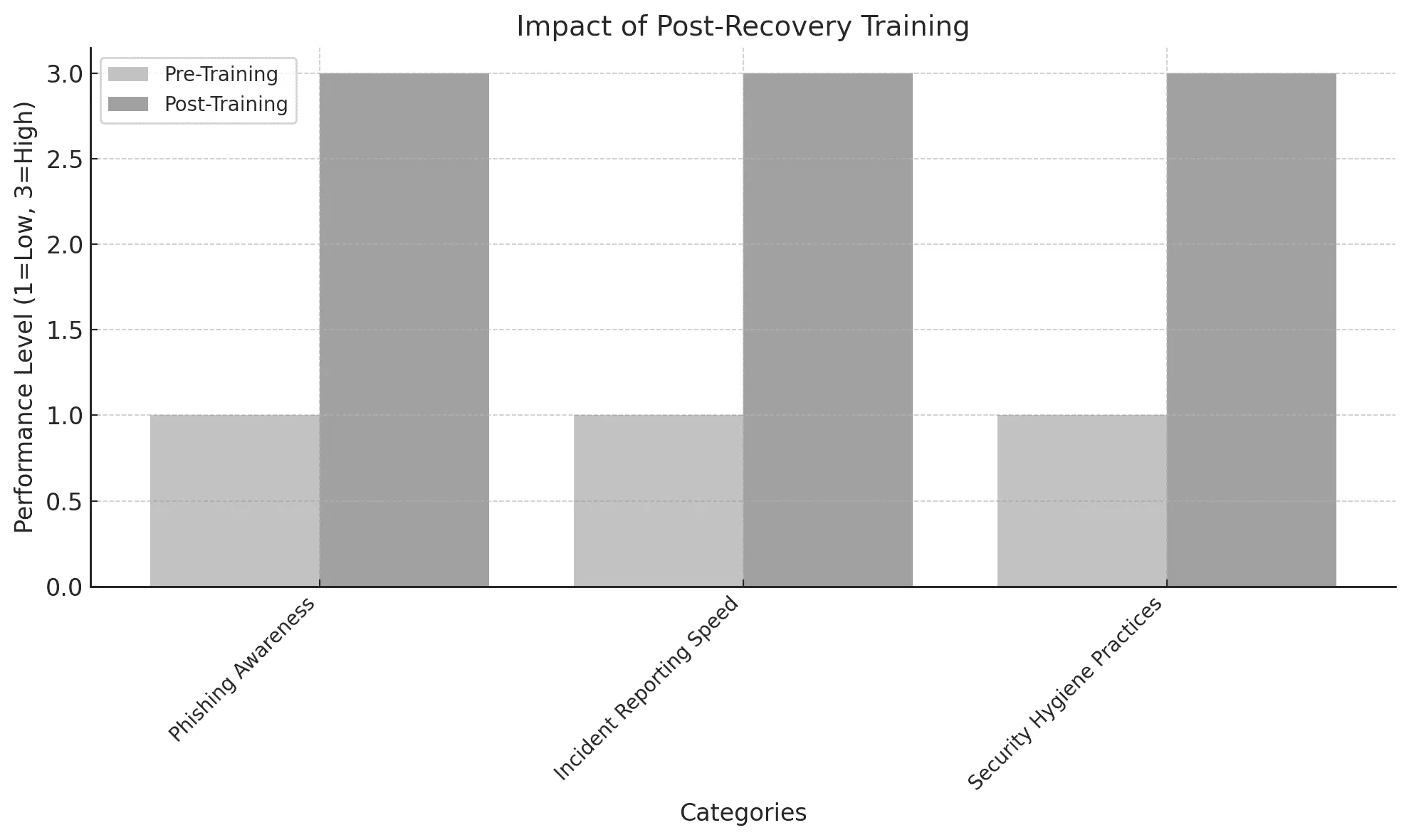
Impact of Post-Recovery Training:
| Category | Pre-Training | Post-Training |
|---|---|---|
| Phishing Awareness | Low | High |
| Incident Reporting Speed | Slow | Immediate |
| Security Hygiene Practices | Poor | Excellent |
🔑 Key Takeaways
- Proactive Cybersecurity Measures: Regular vulnerability assessments are critical to mitigating risks.
- Employee Awareness: Continuous training in phishing and social engineering defense is indispensable.
- Resilient Infrastructure: Advanced tools like Zero Trust, EDR, and SIEM ensure robust defenses against modern threats.
🚀 Next Steps: Explore how our team can enhance your organization’s cybersecurity posture. Get in Touch
By combining swift action, advanced tools, and a culture of resilience, CxLabs transformed a cybersecurity crisis into an opportunity to innovate and fortify their systems. Their journey stands as a testament to the power of preparation, technology, and teamwork.




Hear it straight from Ransomware Attack R&P

"I am immensely grateful for the exceptional work done in fortifying our cybersecurity measures. The swift response and comprehensive recovery efforts spearheaded by the team ensured minimal disruption to our operations. Their expertise in implementing preventive measures has significantly enhanced our security posture and instilled confidence in our organization's ability to mitigate future risks. Thank you for your dedication and professionalism."

Sam Johanas
IT Admin
